☁️Configuring AWS VPC using Ansible☁️
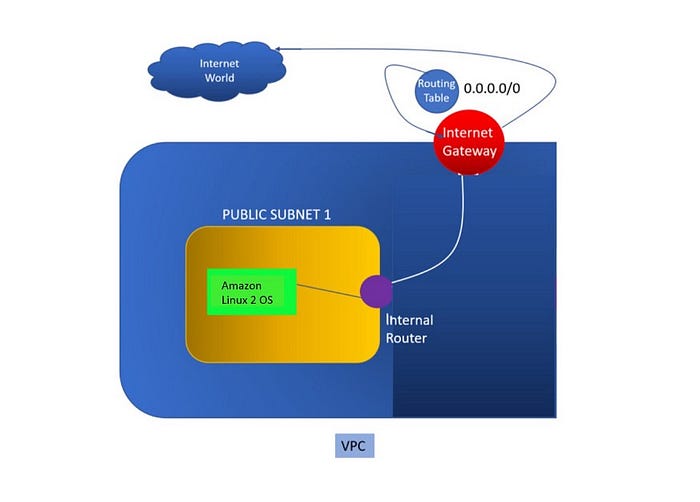
In this article we will see how to configure AWS VPC and launch ec2 instance in one of the subnet inside that VPC using Ansible.
We will configure everything using Ansible Roles.
We need to follow step by step procedure to achieve this:
- Create a VPC (Virtual Private Cloud).
- Create an internet gateway and attach it to VPC.
- Create subnets in that VPC.
- Create Routing table and Routes.
- Create Security group.
- Launch ec2-instances in that subnet of respective VPC.
Create a VPC (Virtual Private Cloud):
To create VPC we need to use ec2_vpc_net module of ansible. We need to provide name of our VPC, cidr_block, region, state to be present etc. The output will register into a variable ec2_vpc_net_result.
tasks file for create-vpc- name: Create VPC over AWS Cloud
ec2_vpc_net:
aws_access_key: "{{ aws_access_key }}"
aws_secret_key: "{{ aws_secret_key }}"
name: "{{ vpc_name }}"
cidr_block: "{{ vpc_cidr_block }}"
region: "{{ region }}"
# enable dns support
dns_support: yes
# enable dns hostnames
dns_hostnames: yes
tenancy: default
state: present
register: ec2_vpc_net_result

Create an internet gateway and attach it to VPC:
Now we need to create internet gateway that will take our requests to internet world. The Igw will be connected to our VPC. We need to specify name of the Igw, the region in which our vpc is located and the state should be present. The output will register into a variable igw_result.
# create an internet gateway for the vpc
- name: Create Internet Gateway for VPC
ec2_vpc_igw:
aws_access_key: "{{ aws_access_key }}"
aws_secret_key: "{{ aws_secret_key }}"
vpc_id: "{{ ec2_vpc_net_result.vpc.id }}"
region: "{{ region }}"
state: present
tags:
Name: "{{ igw_name }}"
register: igw_result
Create Subnet in VPC:
To create a subnet inside above VPC we need to provide the id of the VPC to the subnet. We need to specify availability zone(AZ). A subnet must have a cidr block within the range of cidr block of vpc. If you wanted to have public ip then you need to include map_public as yes. The output will register into a variable subnet_result.
- name: Create VPC Subnet
ec2_vpc_subnet:
aws_access_key: "{{ aws_access_key }}"
aws_secret_key: "{{ aws_secret_key }}"
vpc_id: "{{ ec2_vpc_net_result.vpc.id }}"
region: "{{ region }}"
az: "{{ zone }}" # az is the availability zone
state: present
cidr: "{{ subnet_cidr_block }}"
# enable public ip
map_public: yes
resource_tags:
Name: "{{ subnet_name }}"
register: subnet_result
Create Routing table and Routes:
The routing table is the path we have to specify to the VPC. We need to give vpc_id, subnet, Igw id, region and state to be present. The output of the routing table is stored in public_route_table.
- name: Create VPC Public Subnet Route Table
ec2_vpc_route_table:
aws_access_key: "{{ aws_access_key }}"
aws_secret_key: "{{ aws_secret_key }}"
vpc_id: "{{ ec2_vpc_net_result.vpc.id }}"
region: "{{ region }}"
state: present
tags:
Name: "{{ route_table_name }}"
subnets: [ "{{ subnet_result.subnet.id }}" ] # create routes
routes:
- dest: "{{ destination_cidr_block }}"
gateway_id: "{{ igw_result.gateway_id }}"
register: public_route_table

Creating Security Group
To secure the services we want to run in the respective instances we need to create a firewall. So that our application running on a particular port no. would be safe. ec2_group is the module in ansible to create security group. You need to specify the vpc id i.e. in which vpc you want to create a security group also on which port your services are running and who will access it. The output of the security group is stored inside variable security_group_results.
- name: Create Security Group
ec2_group:
aws_access_key: "{{ aws_access_key }}"
aws_secret_key: "{{ aws_secret_key }}"
vpc_id: "{{ ec2_vpc_net_result.vpc.id }}"
region: "{{ region }}"
state: present
name: "{{ security_group_name }}"
description: "{{ security_group_name }}"
tags:
Name: "{{ security_group_name }}"
rules:
- proto: all
cidr_ip: "{{ port22_cidr_block }}"
rule_desc: allow all traffic
register: security_group_results
Launch ec2-instance in that subnet of respective VPC:
To launch an ec2 instance we need to provide image id, instance type (here we will use t2.micro because it comes in free-tier), key, region, state to be present, vpc_subnet_id, security group_id, access key and secret key etc. If we want to assign public IP to our instance then we can use assign_public_ip as yes.
# tasks file for ec2-launch- name: "Provisioning ec2 instance over AWS Cloud"
ec2:
image: "{{ image_id }}"
instance_type: "{{ instance_type }}"
region: "{{ region }}"
key_name: "{{ key }}"
wait: yes
count: 1
state: present
vpc_subnet_id: "{{ subnet_result.subnet.id }}"
assign_public_ip: yes
group_id: "{{ security_group_results.group_id }}"
aws_access_key: "{{ aws_access_key }}"
aws_secret_key: "{{ aws_secret_key }}"
instance_tags:
Name: "{{ item }}"
loop: "{{ OS_Names }}"
Ansible Roles
> Creating role to create VPC.
ansible galaxy init create-vpc
> Creating role to create ec2-instance.
ansible galaxy init ec2-launchAfter creating ansible roles we need to write the yaml code inside the respective files. we have vars folder to keep variables and tasks folder to write tasks.
vars file to create VPC:
# vars file for create-vpcaws_access_key: "enter access key"
aws_secret_key: "enter secret key"
title: "ARTH"
vpc_name: "{{ title }} VPC"
igw_name: "{{ title }} Igw"
subnet_name: "{{ title }} Subnet"
route_table_name: "{{ title }} Route Table"
security_group_name: "{{ title }} SG"
vpc_cidr_block: '11.0.0.0/16'
subnet_cidr_block: '11.0.1.0/24'
destination_cidr_block: '0.0.0.0/0'
port22_cidr_block: '0.0.0.0/0'
region: "ap-south-1"
zone: "ap-south-1a"
vars file to launch ec2 instance:
# vars file for ec2-launchimage_id: "ami-0eeb03e72075b9bcc"
instance_type: "t2.micro"
region: "ap-south-1"
key: "arth"
aws_access_key: "enter access key"
aws_secret_key: "enter secret key"
OS_Names:
- "EC2-Ansible"
We are creating our main playbook named vpc-setup.yml and putting are roles there.
- hosts: localhost
roles:
- name: "Creating VPC"
role: "/aws-vpc/create-vpc"- name: "Launching ec2-instance"
role: "/aws-vpc/ec2-launch"
The command to execute the playbook :
ansible-playbook vpc-setup.yml
Now we can check the ec2 dashboard, we will see the instance has been created and running successfully.

You can get the code from my github
https://github.com/hrishabhsharma/Configuring-AWS-VPC-using-Ansible
Thanks for reading !!!😊✨ keep Learning!
